Form For End Of Day Security Checks
Form For End Of Day Security Checks - This form ensures that all security measures have been taken and that the premises are secure. This form is used to ensure that all security measures have been met and that no unauthorized persons or activities have taken place. Pdf versions of forms use adobe reader ™. Check all doors and windows to ensure they are locked. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. Web introduction welcome to the department of defense (dod) annual security awareness refresher training! Web how it works open the end of day security checks and follow the instructions easily sign the what form is used for end of day security checks with your finger send filled & signed end of day security checks form or save what. This form is also used to document any incidents that have occurred during the day. Web activity security checklist. Web the standard form (sf) 702 security container check sheet provides a record of the names and times that persons have opened, closed and checked a particular container that holds classified.
This form is used to ensure that all security measures have been met and that no unauthorized persons or activities have taken place. Web regarding security, there is no such thing as being too careful. Pdf versions of forms use adobe reader ™. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. Web introduction welcome to the department of defense (dod) annual security awareness refresher training! Web activity security checklist. This form is also used to document any incidents that have occurred during the day. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. Edit & sign security guard inspection checklist from anywhere. Check all doors and windows to ensure they are locked.
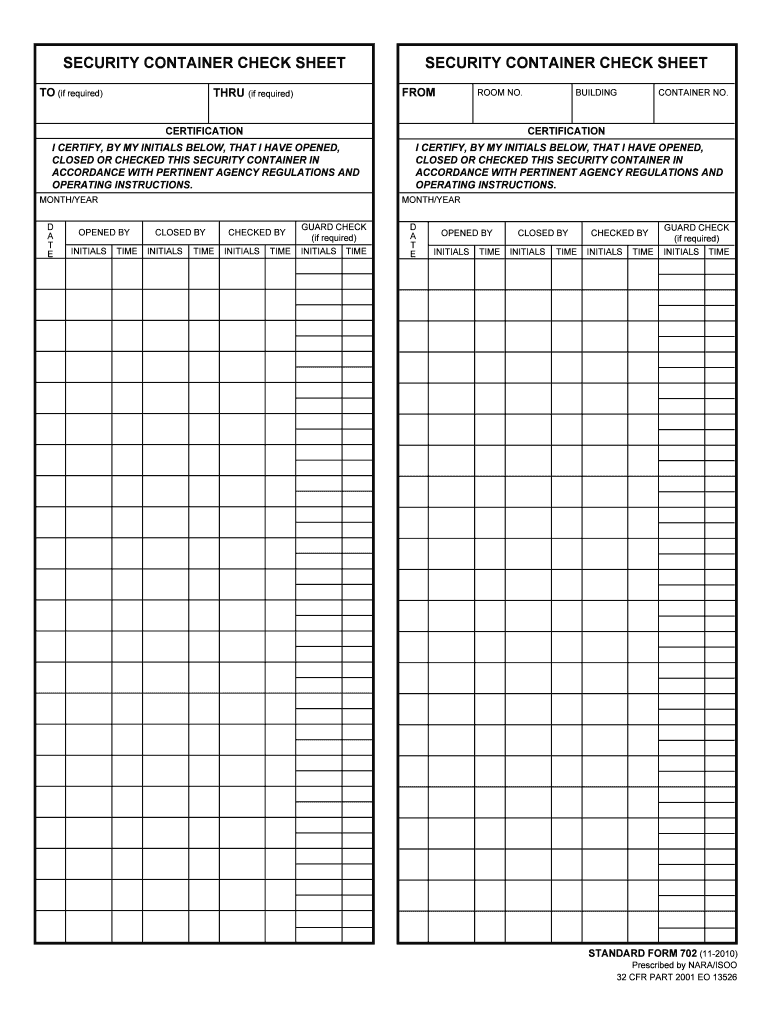
Web the standard form (sf) 702 security container check sheet provides a record of the names and times that persons have opened, closed and checked a particular container that holds classified. Edit & sign security guard inspection checklist from anywhere. This form ensures that all security measures have been taken and that the premises are secure. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. Check all doors and windows to ensure they are locked. The purpose of this training is to provide a review of basic security principles and responsibilities to protect dod assets. Pdf versions of forms use adobe reader ™. Upload the end of day security checks. Web how it works open the end of day security checks and follow the instructions easily sign the what form is used for end of day security checks with your finger send filled & signed end of day security checks form or save what. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure.
Free 4+ Employee End Of Day Report Forms In Word Xls Pdf Throughout
Upload the end of day security checks. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. Check.
Security checks in operation sign CCTV Security Signs Safety Signs
This form ensures that all security measures have been taken and that the premises are secure. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where.
Security Checklist PDF
Edit & sign security guard inspection checklist from anywhere. Upload the end of day security checks. Web activity security checklist. Check all doors and windows to ensure they are locked. Web how it works open the end of day security checks and follow the instructions easily sign the what form is used for end of day security checks with your.
Sf702 PDF SECURITY CONTAINER CHECK SHEET TOif Form Fill Out and Sign
Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. Save your changes and share security guard patrol.
SECURITY CHECKS 14244_226
Pdf versions of forms use adobe reader ™. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure..
The Request Contains No Certificate Template Information Elegant Free 6
This form is also used to document any incidents that have occurred during the day. Upload the end of day security checks. This form is used to ensure that all security measures have been met and that no unauthorized persons or activities have taken place. Web regarding security, there is no such thing as being too careful. Web [narrator:] per.
End of day checks Ensure your retail premises are secure
Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. This form is used to ensure that all.
Security Guard Patrol Checklist Template Fill Online, Printable
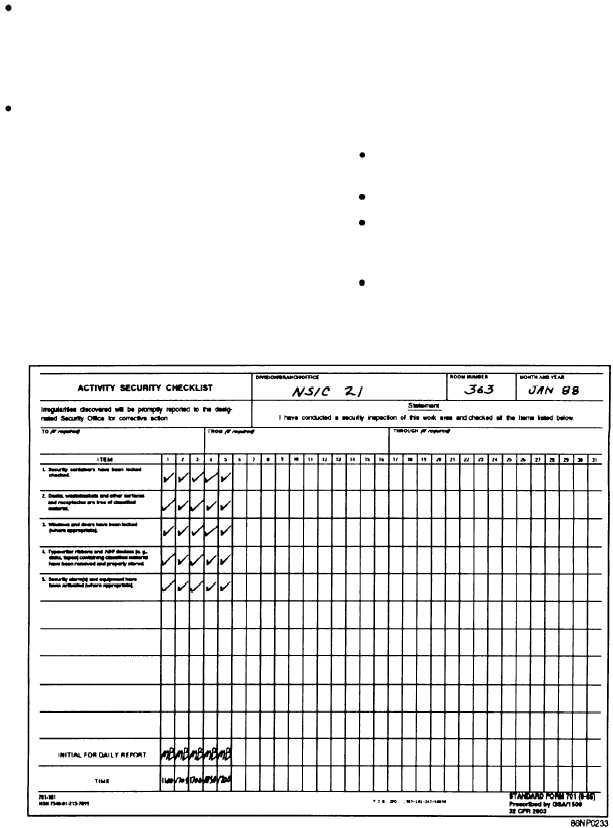
Web activity security checklist. Web regarding security, there is no such thing as being too careful. Web the standard form (sf) 702 security container check sheet provides a record of the names and times that persons have opened, closed and checked a particular container that holds classified. Records management schedules) to ensure availability for audits and resolution of subsequent discovery.
SF 701 Instructions Security Checks Matter
Web how it works open the end of day security checks and follow the instructions easily sign the what form is used for end of day security checks with your finger send filled & signed end of day security checks form or save what. Pdf versions of forms use adobe reader ™. Web regarding security, there is no such thing.
SF 702 Security Container Check Sheet Security Checks Matter
Edit & sign security guard inspection checklist from anywhere. The purpose of this training is to provide a review of basic security principles and responsibilities to protect dod assets. Web regarding security, there is no such thing as being too careful. Upload the end of day security checks. This form is also used to document any incidents that have occurred.
Web Regarding Security, There Is No Such Thing As Being Too Careful.
Pdf versions of forms use adobe reader ™. Web activity security checklist. Web how it works open the end of day security checks and follow the instructions easily sign the what form is used for end of day security checks with your finger send filled & signed end of day security checks form or save what. This form is also used to document any incidents that have occurred during the day.
Save Your Changes And Share Security Guard Patrol Checklist Template.
Edit & sign security guard inspection checklist from anywhere. This form is used to ensure that all security measures have been met and that no unauthorized persons or activities have taken place. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. Check all doors and windows to ensure they are locked.
Web [Narrator:] Per Enclosure 2, Paragraph 9, End Of Day Security Checks, The Heads Of Activities That Process Or Store Classified Information Shall Establish A System Of Security Checks At The Close Of Each Duty And/Or Business Day To Ensure That Any Area Where Classified Information Is Used Or Stored Is Secure.
Upload the end of day security checks. The purpose of this training is to provide a review of basic security principles and responsibilities to protect dod assets. Web introduction welcome to the department of defense (dod) annual security awareness refresher training! This form ensures that all security measures have been taken and that the premises are secure.
Web The Standard Form (Sf) 702 Security Container Check Sheet Provides A Record Of The Names And Times That Persons Have Opened, Closed And Checked A Particular Container That Holds Classified.
Records management schedules) to ensure availability for audits and resolution of subsequent discovery of security incidents or discrepancies.






.jpg)
